The Myth of the "F Key" Lock: Understanding Computer Security
Related Articles: The Myth of the "F Key" Lock: Understanding Computer Security
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Myth of the "F Key" Lock: Understanding Computer Security. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Myth of the "F Key" Lock: Understanding Computer Security

The notion of a dedicated "F key" to lock a computer has persisted in popular culture, often circulating as a convenient shortcut for security. However, this concept is a misconception. There is no universally recognized function key, such as "F1" or "F12," that serves as a direct lock mechanism on any standard computer operating system.
This misconception likely stems from the inherent desire for simplicity and quick solutions in managing computer security. The idea of a single keystroke to safeguard a system resonates with the human desire for ease and efficiency. However, the reality of computer security is far more nuanced and requires a multi-layered approach.
Understanding Computer Security: Beyond the "F Key"
Computer security is a complex field encompassing various layers of protection. These layers include:
- Operating System Security: Modern operating systems implement robust security measures like user accounts, password protection, and access control lists. These features restrict unauthorized access and prevent malicious software from taking control of the system.
- Software Security: Applications and programs also contribute to overall security. Regularly updating software patches and using reputable software sources help mitigate vulnerabilities.
- Hardware Security: Physical security measures like BIOS passwords and hardware encryption play a crucial role in preventing unauthorized access to the computer’s components.
- Network Security: Firewalls, intrusion detection systems, and secure network protocols safeguard the computer from external threats and unauthorized access over the network.
- User Awareness: User education and awareness are paramount. Understanding basic security practices like strong passwords, avoiding suspicious links, and being cautious about phishing attempts is essential to prevent security breaches.
Locking Your Computer: The Right Way
While a single keystroke to lock a computer may not exist, various methods offer reliable security solutions:
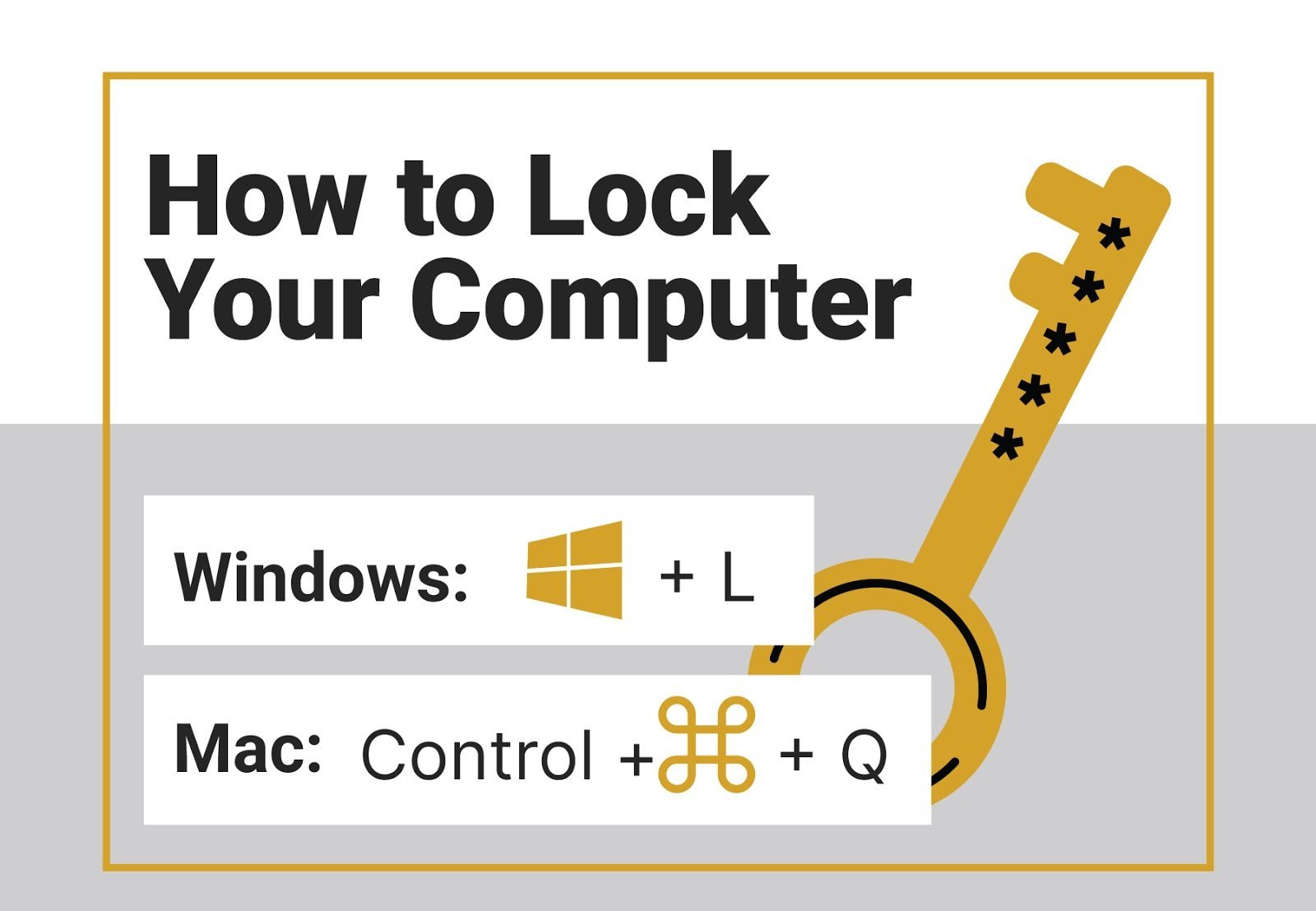
- Operating System Lock: Most modern operating systems offer built-in lock features. These are typically accessed through keyboard shortcuts (e.g., Windows key + L, Ctrl + Alt + Delete), or by using the "Start" menu or system tray.
- Password Protection: Setting a strong password for your user account is essential. A strong password is a combination of uppercase and lowercase letters, numbers, and symbols.
- Screen Lock: Enabling screen lock is a quick and effective way to prevent unauthorized access to your computer when you step away.
- Sleep Mode: Placing your computer in sleep mode reduces energy consumption and suspends operations, effectively locking the system until you wake it up.
- Hibernate Mode: Hibernate mode saves the current state of your computer to the hard drive, allowing you to resume work exactly where you left off.
FAQs: Addressing Common Questions About Computer Security
Q: What are the best practices for securing my computer?
A: Maintaining a secure computer involves a multi-pronged approach. This includes:
- Strong Passwords: Use a unique and strong password for each of your accounts.
- Software Updates: Regularly update your operating system and software applications to patch vulnerabilities.
- Antivirus Software: Install and keep your antivirus software updated to protect against malware.
- Firewall: Enable your firewall to prevent unauthorized access to your computer.
- Be Cautious Online: Avoid clicking suspicious links, downloading files from untrusted sources, and sharing personal information online.
Q: What are the risks associated with not locking my computer?
A: Leaving your computer unlocked poses several risks:
- Unauthorized Access: Anyone can access your files, applications, and personal information.
- Data Theft: Sensitive data, such as financial records, passwords, and personal documents, could be stolen.
- Malware Infection: Your computer could be infected with malware, which can steal your data, compromise your privacy, or damage your system.
- Identity Theft: Your personal information could be used to commit identity theft.
Q: How can I lock my computer remotely?
A: Several methods allow you to lock your computer remotely:
- Remote Desktop Software: Applications like Microsoft Remote Desktop or TeamViewer allow you to connect to and control your computer remotely.
- Mobile Device Management (MDM): MDM solutions offer features to lock, wipe, or track your computer remotely.
- Cloud Services: Some cloud services, like Google Drive, offer file synchronization and remote access, allowing you to lock your computer from a web browser.
Tips for Maintaining Computer Security:
- Regularly back up your data: Regular backups protect your data from accidental loss or corruption.
- Be aware of phishing scams: Phishing emails and websites attempt to trick you into providing personal information.
- Use a password manager: Password managers securely store and manage your passwords.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security by requiring a second verification step, typically a code sent to your phone.
- Stay informed about security threats: Stay updated on the latest security threats and vulnerabilities.
Conclusion: A Holistic Approach to Computer Security
While the concept of a single "F key" to lock a computer is a misconception, it highlights the human desire for simple solutions to complex issues. True computer security involves a multi-faceted approach, encompassing operating system security, software updates, hardware protection, network security, and user awareness. By understanding and implementing these measures, users can effectively safeguard their computers and sensitive information from unauthorized access and potential threats. Remember, computer security is an ongoing process, requiring vigilance and continuous adaptation to evolving threats.







Closure
Thus, we hope this article has provided valuable insights into The Myth of the "F Key" Lock: Understanding Computer Security. We appreciate your attention to our article. See you in our next article!