Securing Your PC: Understanding and Managing Port Access
Related Articles: Securing Your PC: Understanding and Managing Port Access
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Securing Your PC: Understanding and Managing Port Access. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Securing Your PC: Understanding and Managing Port Access
- 2 Introduction
- 3 Securing Your PC: Understanding and Managing Port Access
- 3.1 Understanding Ports and Their Role in Connectivity
- 3.2 The Importance of Port Management
- 3.3 Disabling Ports: A Powerful Security Measure
- 3.4 Benefits of Port Management
- 3.5 Practical Considerations for Port Management
- 3.6 FAQs on Port Management
- 3.7 Tips for Effective Port Management
- 3.8 Conclusion
- 4 Closure
Securing Your PC: Understanding and Managing Port Access
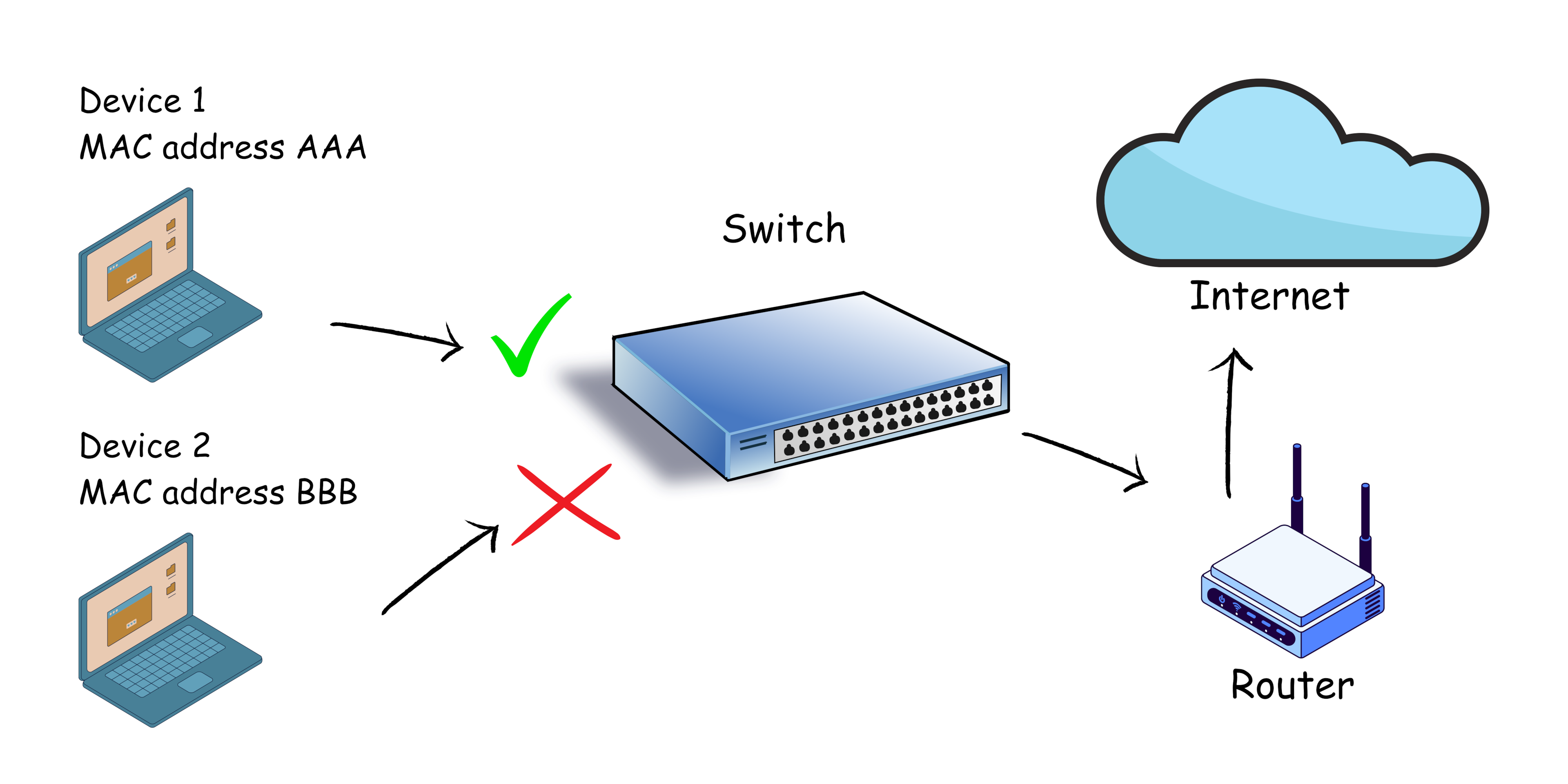
In the digital landscape, a personal computer (PC) serves as a gateway to a vast network of information and services. While this connectivity offers immense benefits, it also presents vulnerabilities. Unauthorized access through open ports can expose sensitive data, compromise system security, and even enable malicious activities. This article delves into the concept of port management, exploring its significance and providing practical insights into how to effectively secure your PC by managing port access.
Understanding Ports and Their Role in Connectivity
Ports, in the context of computer networking, are virtual pathways that allow communication between different applications and services. Each port is assigned a unique numerical identifier, ranging from 0 to 65535, facilitating the flow of data between your PC and external devices or services.
Imagine a bustling airport with numerous gates. Each gate represents a port, channeling passengers (data) to specific destinations (services). While some gates are dedicated to specific airlines (services), others remain open for general use. Similarly, ports on your PC can be associated with specific programs or services, or left open for general access.
The Importance of Port Management
Open ports are like unlocked doors, inviting potential threats into your system. Malicious actors can exploit these open pathways to gain unauthorized access, install malware, steal data, or even launch denial-of-service attacks.
Effective port management involves carefully controlling which ports are accessible and to whom. By selectively disabling unnecessary ports, you create a more secure environment, limiting the potential entry points for attackers.
Disabling Ports: A Powerful Security Measure
Disabling ports involves closing these virtual pathways, effectively blocking communication through them. This process can be implemented at various levels, including the operating system, firewall, and network router.
1. Operating System Level:
Many operating systems offer built-in tools to manage port access. Windows, for instance, provides a command-line utility called "netsh" for managing network settings, including port disabling. This method offers a granular level of control, allowing you to disable specific ports for specific applications or services.
2. Firewall Level:
Firewalls act as security barriers, filtering incoming and outgoing network traffic. Most modern operating systems include built-in firewalls that allow you to block access to specific ports. This approach provides a more general level of security, blocking access to a range of ports simultaneously.
3. Network Router Level:
Routers act as gateways between your local network and the internet. Many routers offer port-forwarding and port-blocking features. By configuring your router to block access to certain ports, you can further enhance the security of your network and prevent unauthorized access to your PC.
Benefits of Port Management
Disabling unnecessary ports offers numerous benefits, including:
- Reduced Vulnerability: By closing unnecessary ports, you significantly reduce the potential attack surface, making it harder for malicious actors to exploit vulnerabilities.
- Improved System Performance: Disabling ports can free up system resources, leading to improved performance and responsiveness.
- Enhanced Privacy: By restricting access to specific ports, you can enhance privacy by preventing unauthorized access to sensitive data.
- Compliance with Security Standards: Many organizations and institutions require adherence to specific security standards, which may include port management practices.
Practical Considerations for Port Management
While disabling ports is a crucial security measure, it’s important to proceed with caution and consider the following:
- Essential Ports: Ensure that you do not disable ports required for essential system services or applications. For example, ports used for web browsing, email communication, or remote access may need to remain open.
- Application Compatibility: Disabling ports may interfere with certain applications or services. Before disabling any port, check the application’s documentation or contact the developer to confirm compatibility.
- Port Scanning: Use port scanning tools to identify which ports are currently open on your PC. This information can help you determine which ports can be safely disabled.
- Regular Monitoring: It’s crucial to monitor your system regularly for any changes in port access or suspicious activity.
FAQs on Port Management
1. What are the most common ports that should be disabled?
The ports that should be disabled depend on your specific needs and the applications you use. However, some commonly disabled ports include:
- Port 21: FTP (File Transfer Protocol), often used for file sharing, can be a target for malware.
- Port 22: SSH (Secure Shell), used for remote access, should be disabled if not actively used.
- Port 23: Telnet, an older protocol for remote access, is generally considered insecure and should be disabled.
- Port 80: HTTP (Hypertext Transfer Protocol), used for web browsing, can be exploited if not properly secured.
- Port 443: HTTPS (Hypertext Transfer Protocol Secure), used for secure web browsing, is generally safe to leave open.
2. Can I disable ports permanently?
It’s generally recommended to disable ports temporarily unless you have a specific reason to disable them permanently. Disabling ports permanently may interfere with the functionality of certain applications or services.
3. How do I know which ports are required for my applications?
You can consult the documentation for your applications or contact the developer for information on required ports. You can also use port scanning tools to identify which ports are currently in use.
4. Is disabling ports a foolproof security measure?
Disabling ports is a valuable security measure, but it’s not a foolproof solution. Malicious actors can still exploit other vulnerabilities or use alternative methods to gain access to your system.
5. What are some other security measures I can take?
In addition to port management, other security measures include:
- Strong Passwords: Use strong passwords for all your accounts and avoid using the same password for multiple accounts.
- Regular Software Updates: Keep your operating system and applications up-to-date with the latest security patches.
- Antivirus Software: Install and maintain antivirus software to detect and remove malware.
- Firewall: Enable and configure your firewall to block unauthorized access.
- Security Awareness: Stay informed about common online threats and practice safe browsing habits.
Tips for Effective Port Management
- Start with a Baseline: Identify the essential ports required for your applications and services.
- Prioritize Security: Disable ports that are not actively used and pose a potential security risk.
- Document Changes: Keep a record of any port changes you make, including the date, reason, and affected ports.
- Regular Review: Periodically review your port settings and make adjustments as needed.
- Use a Network Monitoring Tool: Monitor network activity for any suspicious behavior or attempts to access disabled ports.
Conclusion
Disabling unnecessary ports is a crucial step in securing your PC against malicious actors. By carefully managing port access, you can create a more secure environment, limiting the potential entry points for attackers and protecting your sensitive data. Remember, port management is an ongoing process that requires vigilance and regular adjustments to maintain optimal security. By implementing these practices, you can significantly enhance the security of your PC and safeguard your digital world.



:max_bytes(150000):strip_icc()/computer-port-usage-817366FINALv1-afe07fea146e42b9b002e78809faad61.jpg)
Closure
Thus, we hope this article has provided valuable insights into Securing Your PC: Understanding and Managing Port Access. We hope you find this article informative and beneficial. See you in our next article!