Navigating the Landscape of Windows 11 Execution Policies: A Comprehensive Guide
Related Articles: Navigating the Landscape of Windows 11 Execution Policies: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Landscape of Windows 11 Execution Policies: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Landscape of Windows 11 Execution Policies: A Comprehensive Guide

Windows 11, like its predecessors, implements execution policies to govern the execution of scripts and applications within the operating system. These policies are designed to enhance system security by controlling the origin and trustworthiness of executable files, thereby mitigating the risk of malicious code execution. Understanding and effectively utilizing these policies is crucial for maintaining a secure and stable Windows 11 environment.
Understanding the Core Concepts:
Execution policies in Windows 11 are primarily enforced through the Windows PowerShell environment. They determine which scripts can be executed, and under what conditions, by defining specific levels of trust. The policies are configured using the Set-ExecutionPolicy cmdlet, and their settings are stored within the registry, making them persistent across system restarts.
The Spectrum of Execution Policies:
Windows 11 offers a range of execution policies, each providing a distinct level of security and flexibility:
- Restricted: This policy, the most restrictive, prohibits the execution of any scripts. It is ideal for environments where script execution is strictly controlled and only authorized applications are allowed.
- AllSigned: This policy allows only scripts signed by a trusted publisher to execute. It provides a strong security measure by requiring digital signatures for verification, ensuring the authenticity and integrity of the code.
- RemoteSigned: This policy permits the execution of scripts downloaded from the internet or other untrusted sources, provided they are signed by a trusted publisher. This approach allows for greater flexibility while maintaining a level of security.
- Unrestricted: This policy, the least restrictive, allows the execution of any script without any restrictions. While offering the most flexibility, it exposes the system to potential security risks.
- Bypass: This policy completely disables the execution policy mechanism, allowing scripts to run without any checks. It is primarily used for debugging purposes and should not be implemented in production environments.
The Importance of Execution Policies:
The implementation of execution policies in Windows 11 is critical for several reasons:
- Security Enhancement: Execution policies significantly bolster system security by preventing the execution of potentially malicious scripts or applications. They act as a critical line of defense against malware and other threats.
- Code Integrity: By requiring digital signatures, execution policies ensure the integrity and authenticity of the executed code, minimizing the risk of unauthorized modifications or malicious tampering.
- Policy Enforcement: Execution policies provide a consistent and enforced mechanism for managing script execution across the entire system, promoting a standardized and secure environment.
- Risk Mitigation: By controlling script execution based on their origin and trustworthiness, execution policies significantly reduce the risk of accidental or malicious code execution, safeguarding the system and its data.
Configuration and Management:
Configuring execution policies in Windows 11 is a straightforward process achieved through the Windows PowerShell console. The following steps outline the process:
-
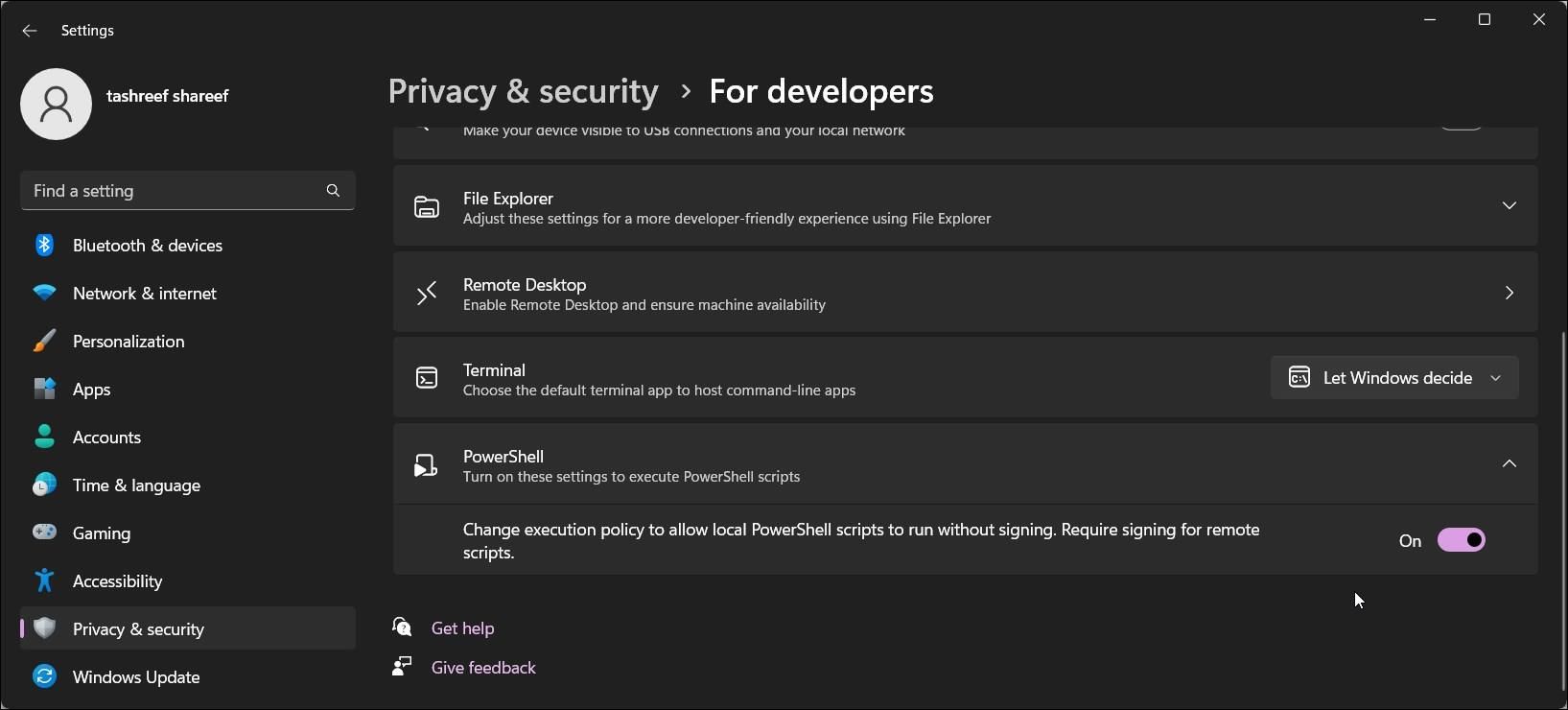
Open Windows PowerShell: Access the Windows PowerShell console by searching for it in the Start menu and running it with administrator privileges.
-
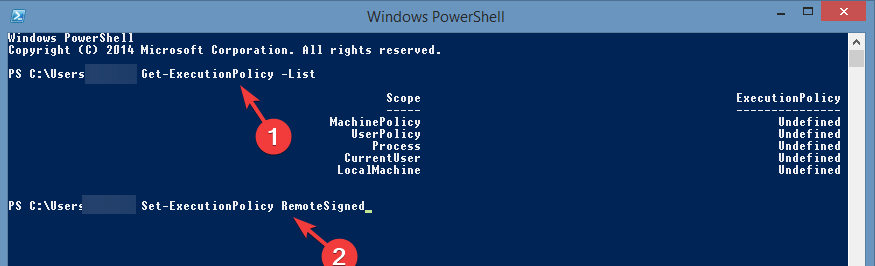
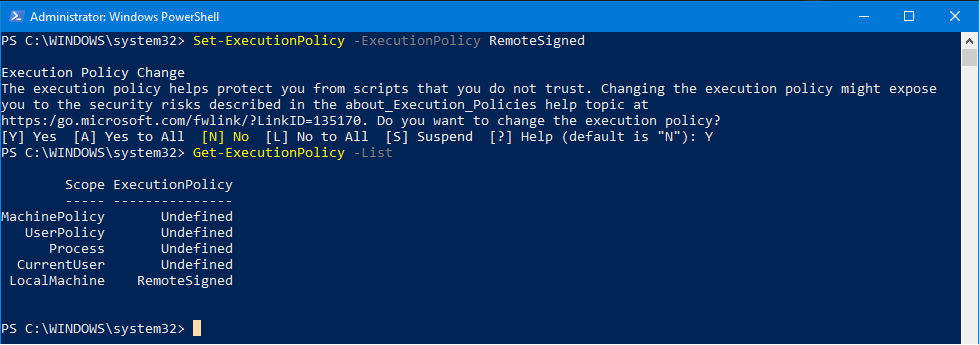
Execute the Set-ExecutionPolicy Cmdlet: Use the following command to set the desired execution policy:
Set-ExecutionPolicy <policy_name>Replace
<policy_name>with the desired policy from the list above (e.g.,Restricted,AllSigned,RemoteSigned,Unrestricted,Bypass). -
Confirm the Policy Change: After executing the command, the system will prompt for confirmation. Choose ‘Yes’ to apply the new policy.
-
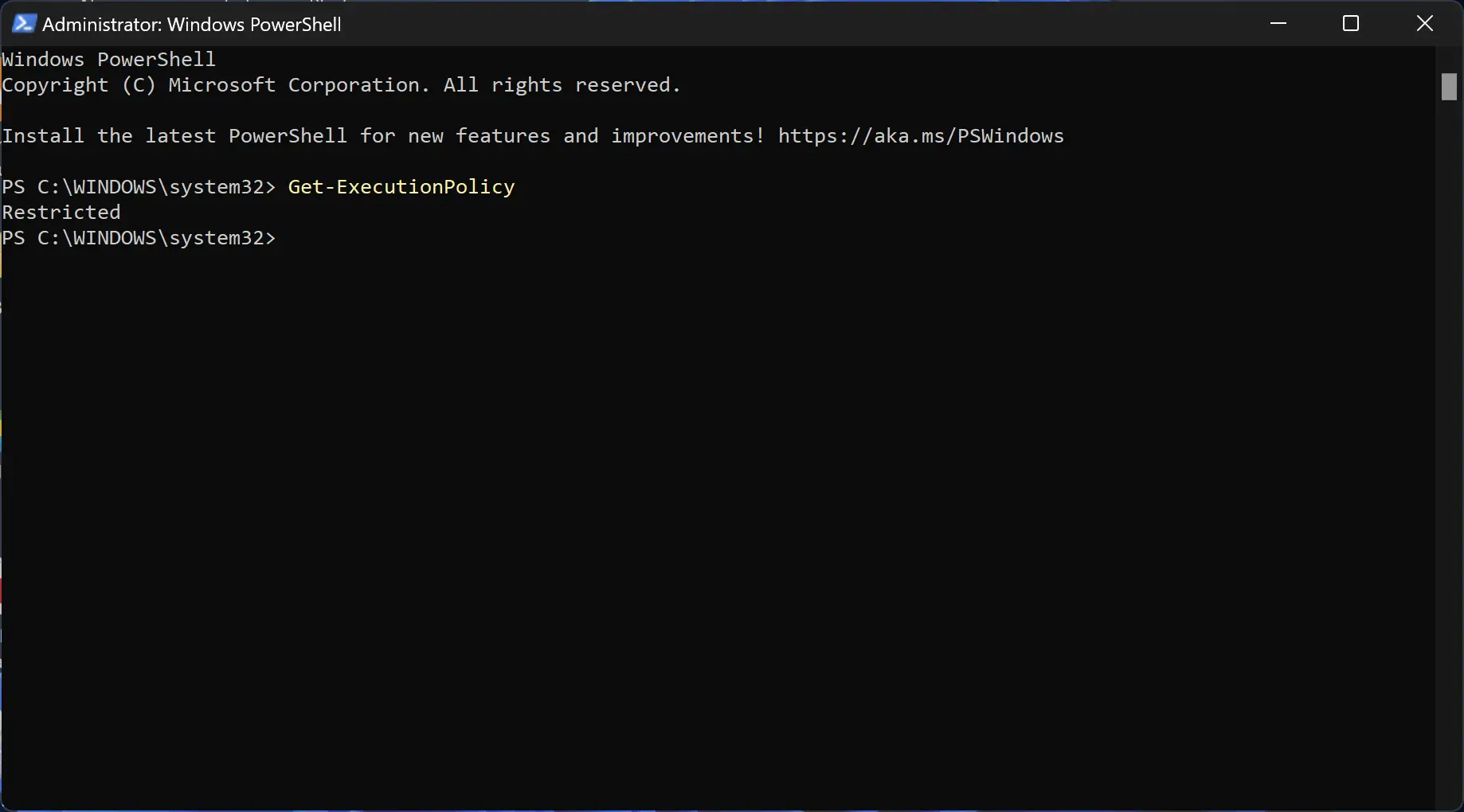
Verify Policy Settings: To verify the current execution policy, use the following command:
Get-ExecutionPolicyThe output will display the currently configured policy.
Best Practices for Execution Policies:
- Choose the Appropriate Policy: Select the most restrictive policy that still allows the necessary functionality for your environment.
- Implement Strong Password Policies: Secure your system with strong passwords to prevent unauthorized access and policy changes.
- Regularly Review and Update Policies: As security threats evolve, periodically review and update execution policies to ensure they remain effective.
- Utilize Digital Signatures: Encourage the use of digital signatures for scripts to enhance their trustworthiness and minimize the risk of malicious code.
- Educate Users: Inform users about the importance of execution policies and how they contribute to system security.
FAQs on Windows 11 Execution Policies:
Q: What happens if I run a script without the necessary permissions based on the execution policy?
A: The script will fail to execute, and an error message will be displayed indicating the reason for the failure.
Q: Can I configure different execution policies for different users or groups?
A: Yes, you can configure different execution policies for specific users or groups by using the -Scope parameter in the Set-ExecutionPolicy cmdlet.
Q: What if I need to execute a script that requires a specific execution policy?
A: You can temporarily bypass the execution policy for a specific script by using the -ExecutionPolicy parameter in the command line or by using the Bypass policy for specific scenarios.
Q: How do I troubleshoot execution policy issues?
A: You can use the Get-ExecutionPolicy cmdlet to verify the current policy settings and troubleshoot any discrepancies. Additionally, you can check the Windows event logs for error messages related to script execution.
Q: Is it possible to completely disable execution policies?
A: While you can use the Bypass policy to disable execution policy checks, it is not recommended for production environments as it significantly compromises system security.
Tips for Effective Execution Policy Management:
- Document Policies: Maintain a clear and concise documentation of all configured execution policies, including their rationale and any exceptions.
- Implement Automated Policies: Utilize Group Policy Objects (GPOs) or other automated mechanisms to enforce consistent execution policies across the organization.
- Regularly Monitor for Policy Violations: Implement monitoring tools to detect and address any unauthorized script execution attempts.
- Stay Informed: Stay updated on the latest security threats and best practices for managing execution policies.
Conclusion:
Execution policies are an essential component of a robust security strategy for Windows 11. By carefully configuring and managing these policies, organizations can significantly mitigate the risk of malicious code execution, protect their systems from threats, and maintain a secure and stable operating environment. Understanding the various policy levels, their benefits, and best practices for implementation is crucial for maximizing the security benefits of Windows 11. Regular review, adaptation, and awareness of evolving threats are essential for ensuring the ongoing effectiveness of execution policies in safeguarding systems against malicious activities.



Closure
Thus, we hope this article has provided valuable insights into Navigating the Landscape of Windows 11 Execution Policies: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!