Exploring the Risks and Ethical Considerations of Unauthorized Software Usage
Related Articles: Exploring the Risks and Ethical Considerations of Unauthorized Software Usage
Introduction
With great pleasure, we will explore the intriguing topic related to Exploring the Risks and Ethical Considerations of Unauthorized Software Usage. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Exploring the Risks and Ethical Considerations of Unauthorized Software Usage
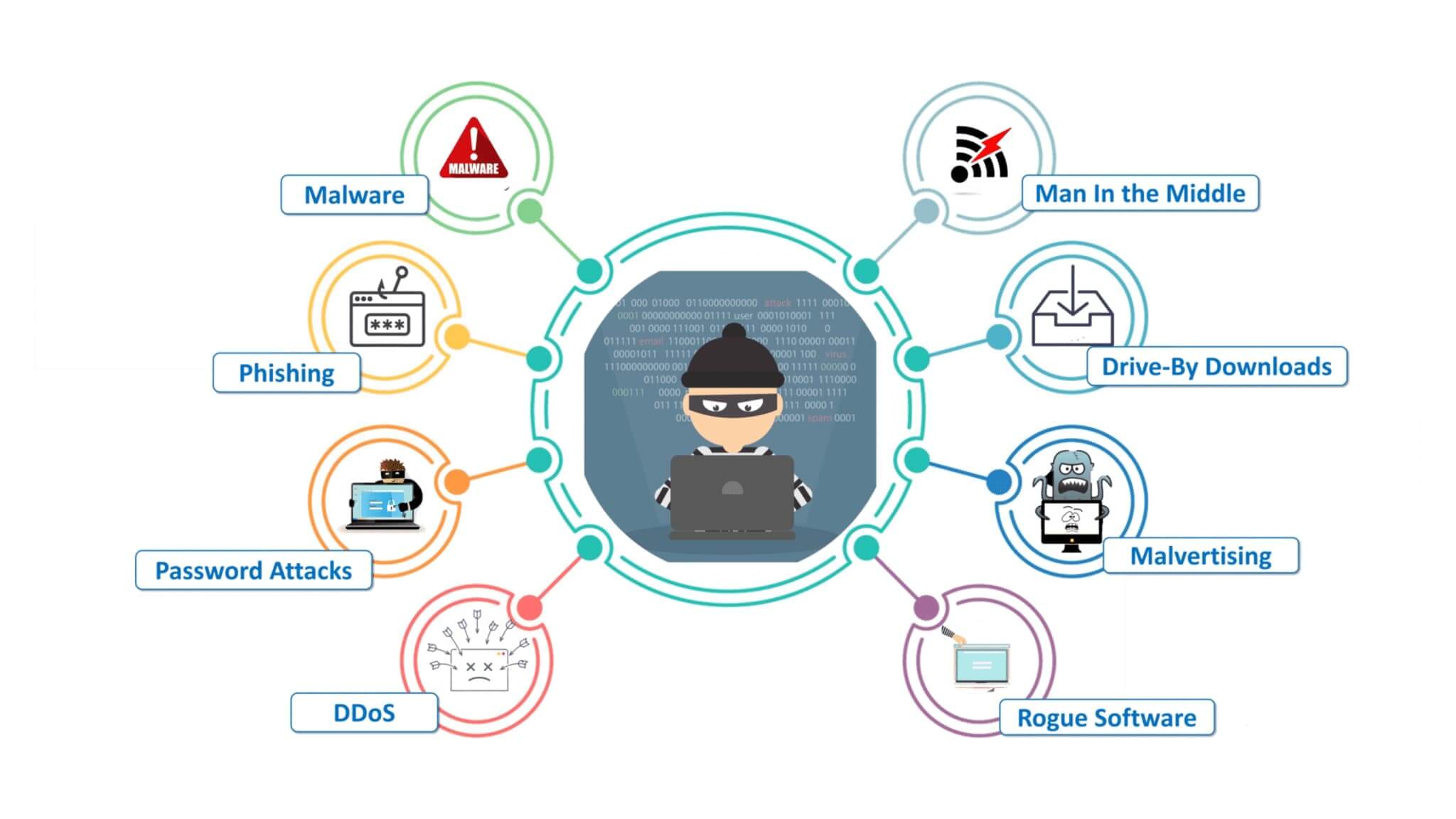
The use of unauthorized software, often referred to as "cracking," is a complex issue with significant legal and ethical ramifications. This article will delve into the intricacies of unauthorized software usage, focusing on the context of Microsoft Office 365 and Windows 11, without endorsing or promoting such practices.
Understanding the Legal Landscape
Software, including operating systems and productivity suites like Microsoft Office 365, is protected by copyright law. Copyright protects the original expression of an idea, granting the creator exclusive rights to reproduce, distribute, and modify their work. When individuals or organizations use software without a valid license, they are violating these legal rights.
Consequences of Unauthorized Software Usage
The consequences of using unauthorized software can be substantial and far-reaching:
- Legal Penalties: Individuals and organizations found guilty of copyright infringement can face significant fines, imprisonment, and legal fees.
- Security Risks: Unauthorized software often lacks proper security measures, leaving systems vulnerable to malware, data breaches, and other cyber threats.
- Lack of Support: Users of unauthorized software are typically ineligible for official technical support, leaving them to resolve issues independently.
- Performance Issues: Unauthorized software may be unstable, prone to crashes, and lack the performance optimization of legitimate versions.
- Ethical Concerns: Using unauthorized software contributes to a culture of disrespect for intellectual property and can undermine the financial stability of software developers.
The Allure of Unauthorized Software
Despite the risks, individuals and organizations may be tempted to use unauthorized software due to several factors:
- Cost Savings: The high cost of legitimate software licenses can be a significant barrier, especially for individuals or small businesses with limited budgets.
- Accessibility: Unauthorized software can be easily obtained through various online sources, often without the need for complex installation procedures.
- Fear of Complexity: The licensing process for legitimate software can be perceived as complicated or time-consuming, leading some to seek simpler solutions.
Exploring Alternatives to Unauthorized Software
Instead of resorting to unauthorized software, individuals and organizations have several ethical and legal alternatives:
- Free and Open-Source Software: There are numerous free and open-source alternatives to commercial software, such as LibreOffice for productivity and Linux for operating systems.
- Subscription Models: Microsoft offers subscription-based models for Office 365, providing access to the latest features and updates at a lower monthly cost than traditional perpetual licenses.
- Educational Discounts: Students, educators, and institutions often qualify for significant discounts on software licenses.
- Cloud-Based Solutions: Cloud-based solutions like Google Workspace offer affordable and accessible alternatives to traditional software installations.
Understanding the Risks of Using Unauthorized Software
It is crucial to understand the inherent risks associated with using unauthorized software:
- Malware and Viruses: Unauthorized software sources are often riddled with malware and viruses that can compromise system security and steal personal data.
- Data Loss and Corruption: Unauthorized software may lack proper data saving mechanisms, leading to potential data loss or corruption.
- System Instability: Unauthorized software can cause system instability, leading to crashes, slowdowns, and other performance issues.
- Legal Liability: Individuals and organizations using unauthorized software can be held legally liable for copyright infringement.
The Importance of Ethical Software Usage
Ethical software usage is paramount for maintaining a healthy digital ecosystem. By respecting intellectual property rights and using legitimate software, individuals and organizations contribute to:
- Supporting Innovation: Software developers rely on revenue generated from legitimate sales to fund further research, development, and innovation.
- Protecting Data: Legitimate software includes security features designed to protect user data from malicious attacks.
- Promoting a Fair Market: Ethical software usage creates a level playing field for software developers and encourages competition.
FAQs Regarding Unauthorized Software
Q: Is it illegal to download and use cracked software?
A: Yes, downloading and using cracked software is illegal in most jurisdictions and can lead to severe consequences.
Q: What are the risks of using cracked software?
A: Cracked software poses significant risks, including malware infection, data loss, system instability, and legal penalties.
Q: Are there any legal alternatives to cracked software?
A: Yes, there are many legal alternatives, including free and open-source software, subscription-based models, educational discounts, and cloud-based solutions.
Q: How can I protect myself from using cracked software?
A: You can protect yourself by using legitimate software sources, avoiding suspicious websites, and keeping your system updated with the latest security patches.
Tips for Ethical Software Usage
- Use legitimate software sources: Download software from trusted vendors and official websites.
- Check for valid licenses: Verify the authenticity of software licenses before purchasing or downloading software.
- Consider subscription models: Explore subscription-based software options that offer access to the latest features and updates at a lower cost.
- Explore free and open-source alternatives: Consider using free and open-source software for tasks that do not require proprietary features.
- Educate yourself on copyright law: Understand the legal implications of using unauthorized software.
Conclusion
While the allure of unauthorized software may be tempting, the risks and ethical implications are significant. It is crucial to prioritize ethical software usage, supporting innovation, protecting data, and promoting a fair market. By choosing legal and ethical alternatives, individuals and organizations can contribute to a healthy digital ecosystem while ensuring their own security and well-being.





Closure
Thus, we hope this article has provided valuable insights into Exploring the Risks and Ethical Considerations of Unauthorized Software Usage. We thank you for taking the time to read this article. See you in our next article!